Compared with identification technologies such as bar code technology, radio frequency identification (RFID) technology has the advantages of waterproof and antimagnetic, long reading distance, more storage data, and data encryption. It has been widely used in transportation, logistics, medical care, food safety, etc. field. However, as an important sensing device of the Internet of Things, it lacks an effective security mechanism, which affects the application and promotion of the Internet of Things. The RFID system security problem and its solution are analyzed from the perspectives of physical security, communication security and information security.
0 Preface
At present, the Internet of Things is gradually being widely used by people. It can connect people with countless items around them, making items become a part of users in the network and bringing convenience to people. However, while enjoying the convenience of the Internet of Things for human convenience, the Internet of Things also needs to be solved in terms of information security, because the realization of information security and network security is a necessary condition for the large-scale application of the Internet of Things, and an important indicator for the maturity of the Internet of Things application system. 1].
As one of the important devices of the Internet of Things sensing layer, RFID technology has the advantages of waterproof and antimagnetic, long reading distance, fast reading speed, large storage capacity, data encryption, pollution and durability, and reusability. It is widely used in transportation, logistics, medical, food safety, retail, manufacturing, customs, security, airport and other applications. It can be seen that the security of RFID systems is directly related to the promotion of Internet of Things security and applications. In addition, the leakage of label information, such as passports, ID cards, prescriptions, etc., will invade personal privacy. Therefore, the security of RFID systems has always been a hot issue of research.
The most basic RFID system consists of the following three parts:
(1) Label: Also known as electronic label, smart card, identification card or identification card, it consists of embedded microprocessor and its software, card transmitting and receiving antenna, and transceiver circuit. The tag is an information carrier that contains a built-in antenna for communication with the RF antenna.
(2) Reader: A device that reads/writes tag information.
(3) Back-end database: used to store related data corresponding to the tag identifier
In general, communication between the reader and the back-end database can be considered safe and reliable. The key is the security of labels and readers. Therefore, we mainly divide the security of RFID systems into three aspects: physical security, communication security, and information security.
1 RFID physical security
RFID reader forgery is a major threat to RFID systems. The communication between the RFID reader and the host can be intercepted by the traditional attack method, and the RFID reader is naturally the object of the attacker.
Electronic tag forgery is another major threat to RFID systems. If criminals can easily falsify electronic tags, it means that they can tamper with the identity of goods or people, and easily damage the credit of RFID systems. For example, in the field of RFID anti-counterfeiting applications, the illegal forgery of RFID means the failure of the anti-counterfeiting system. At present, the main countermeasure against counterfeiting is to increase the cost of forgery by means of ID encryption and special processing. In addition, in order to prevent the reuse of RFID, a special process is used to firmly fix the RFID to the opening of the article, and once the article is opened, the tag is damaged and cannot be reused. For example, in the anti-counterfeiting application of wine, the RFID is embedded in the cork, and as long as the cork is opened, the RFID inside is destroyed and cannot be reused.
RFID collisions affect the normal operation of the RFID system. With the increasing use of RFID technology, multiple tags entering the identification area and signals interfering with each other are inevitable in many cases, and RFID conflicts are becoming more prominent. RFID system conflicts mainly include tag conflicts and reader conflicts.
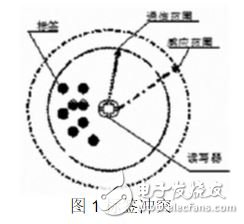
(1) Label conflicts. In RFID systems, when multiple tags enter the read/write area of ​​a reader, conflicts occur, and conflicts can lead to misreading and missing reading. As shown in Figure 1, the conflict also causes the reader to read data efficiently, which eventually causes some tags to be unrecognized in the reader area.
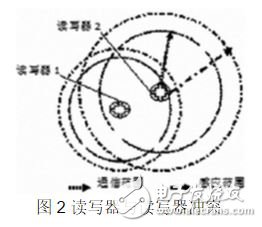
(2) The conflict between the reader and the reader. When two or more readers are close together, one reader will be interfered by the signal of the other reader. When one of the readers is interfered by other readers, the reader will read the data less efficiently or misread, as shown in Figure 2.
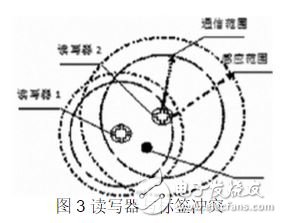
(3) The reader conflicts with the tag. In the reader network, when one or more tags are in the reading range of two or more readers at the same time, the reader conflicts. As shown in Figure 3, there is a tag in the area where both the reader/writer 1 and the reader/writer 2 can be read. The tag is repeatedly read by the reader/writer 1 and the reader/writer 2, or the tag cannot determine the signal to be sent. Which reader, which leads to a decrease in the efficiency of the reader and a confusing read data.
At present, the interference problem of multiple readers on tags is mainly solved by the anti-interference ability of the tags themselves. For the problem of reader collision, people first consider installing according to the principle that the reader's readable range does not overlap during the installation of the project. However, because the RFID reader has high sensitivity, it can even accept 1 space. The energy of Nava, so the readers collided with each other between the readers with far-reaching read/write ranges. At present, solutions to multi-reader collision problems include time slot allocation, channel allocation, carrier sensing, and power control.
2 RFID communication security
RFID uses a wireless communication channel, which brings convenience to illegal users. The attacker can illegally intercept the communication data; the communication link can be blocked by transmitting the interference signal, the reader is overloaded, the normal tag data cannot be received, and the DoS attack can be generated; the data can be sent to the RFID, tampering or forging the data.
(1) Use encryption to ensure data security. Due to the large number and wide range of RFID tags, the cost must be controlled at a relatively low level. This makes RFID tags usually only have about 5,000-10 000 logic gates, and these logic gates are mainly used to achieve some of the most The basic tag feature, only a few left for security features. However, the AES (advanced encrypTIon standard) algorithm requires about 20 000-30 000 logic gates. Public key cryptography algorithms such as RSA and elliptic curve cryptography require more logic gates. Therefore, the literature [4] proposes a secure communication protocol to solve these problems in the case of limited computing resources of RFID tag chips. The protocol uses Hash function technology to prevent security attacks such as message leakage, camouflage, and location tracking. Because of the existing technology and chip manufacturing level, it takes about 3,000 to implement mature hash algorithms such as SHA-l in tag tag chips. - 4 000 logic gates, based on the Hash function of the secure communication protocol, to ensure the security of data transmission between the tag and the reader, while preventing the leakage of the personal information and location information carried by the tag during transmission.
(2) The Gen-2 authentication protocol improves security. The Gen-2 tag for RFID systems has a limited capacity and only supports the single-chip 16-bit pseudo-random number generator (PRNG) and the cyclic redundancy code (CRC) check for error detection during data transmission. To implement complex security algorithms, the literature [5] overcomes the weakness of using the hash function to increase the cost of label design. A Gen-2 tag-based RFID authentication protocol is proposed. The XOR-based method is chosen to divide the 32-bit ID number of the tag. The lower 16 bits and the upper 16 bits use the CRC-16 bits of the tag to generate the corresponding check code as the ciphertext transmission. The protocol solves the security problems of the existing protocols in terms of information confidentiality, non-trackability, forward security, tag anti-cloning and non-reproducibility, which improves the database query speed and reduces the design of RFID tags. cost.
(3) Illegal interception of the wireless signal of the reader. The output power of the reader is much larger than that of the passive electronic tag, so the distance of the reader is much farther than that of the passive electronic tag, such as the maximum communication distance between the UHF reader and the passive electronic tag. It is about 5 meters, which is mainly limited by the power of the electronic tag and the size of the antenna, and the electric wave of the reader itself can travel far away. If someone sets up an antenna to intercept the radio signal of the reader at a distance from the reader, it is difficult to detect. Obtaining information by intercepting the radio waves emitted by the reader is a very professional task, which requires a very large cost. The general RFID system does not need to consider this information leakage risk, but for some confidential information. It is necessary to consider preventive measures, such as closing the reader's working space with absorbing materials and appropriately reducing the output power of the reader.
3 RFID data security
The most important security risk in RFID systems is "data confidentiality." Information leakage refers to the disclosure of the label sending information, which includes information about the label user or the identification object. For example, RFID device management information is public, but when an electronic tag is applied to a drug, it is likely to expose the pathology of the drug user. When personal information such as electronic files and biometrics are added to electronic tags, the leakage of tag information greatly jeopardizes personal privacy. The United States’ plan to equip electronic passports in entry passports in August 2005 has been postponed because of the security concerns of information disclosure.
(1) Stealing electronic tag data. Electronic tags may contain company-critical information or personal privacy information, such as production batches, production quantities, personal identities, shopping habits, etc. If these electronic tags are stolen, it means that internal corporate information or personal privacy information is leaked. In order to prevent data theft, the following two methods can be used: (1) Data encryption. (2) The electronic tag does not store sensitive data, only the ID information without special meaning is stored, and the key data is dispersed in each server.
(2) Tampering with electronic tag data. If you tamper with the data of the electronic tag, it may cause illegal goods or data to be easily mixed into the overall business system, and ultimately disrupt the operation of the business. The main methods to prevent data from being tampered with are: (1) Limiting the number of times the memory is written. If the tag does not need to change in the overall business process, you can use a read-only tag or a one-time read and write tag. Cut off the physical means of tampering with data. (2) Limit the writable area of ​​the memory. The area of ​​the memory is divided into a writable area and a non-writable area in advance, and key data (such as a tag ID) is placed in a non-writable area to prevent tampering of key data. (3) Password protection. The password is pre-set to protect the data. The password of each label is different, and the password management cost needs to be increased. (4) Change the memory area read and write attributes. Setting a read-only attribute on a critical data area or the entire area prevents tampering. The four measures can be used individually or in combination depending on the cost.
(3) Implanting a virus into an electronic tag. Since the electronic tag has a small amount of storage and stores data instead of executing code, it is difficult to write the virus itself into the tag body, but tampering with parameter variables (such as data length, etc.) in the memory disturbs the possibility of system processing. If the middleware and server software are strictly scheduled, the system can be guaranteed to operate normally. At present, there are no reports on actual cases in which viruses are implanted in electronic tags, causing system crashes. There is no anti-virus measures for finished electronic tags. However, with the development of large-capacity and high-intelligence of electronic tags, it is necessary to study viruses in the future. Parasitic mechanisms and preventive measures.
(4) Leaking the electronic tag data format. The electronic tag data format needs to be kept secret. If the data is leaked, it is easy for the criminals to forge and tamper with the tag. Some important data needs to be decentralized, that is, all data cannot be concentrated on one person, in case all the data is exposed once that person is in trouble. It is necessary to strictly manage the production of labels, such as setting up an access control system and installing a computer operation record tracking system.
The user information and privacy issues are becoming more and more prominent. Considering that the RFID authentication protocol based on public key encryption is relatively secure based on the hash function and the RFID authentication protocol based on symmetric key encryption, the literature [6] relies on efficiency. The high public key encryption algorithm NTRU (Number Theory Research Unit) has developed a new RFID protocol that provides better security for RFID systems and provides users with better privacy protection. Table 1 shows the literature [6] ] Better than the performance of the literature [7-9].
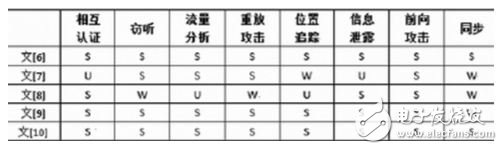
Table 1 Comparison of security of RFID authentication protocol
In [11], the chaotic sequence generated by the chaotic system is used to encrypt the data transmitted between the reader and the tag in the RFID system, and a security model of the RFID system based on chaotic encryption technology is established.
In order to solve several common RFID security problems such as cloning attacks, retransmission attacks, and tag tracking, the literature [12] proposes an improved, more secure, and applicable method based on the analysis of the single certifier interaction model. Based on the model, a multi-certifier interaction proof model of RFID is proposed. Based on this model, an RFID security protocol based on elliptic curve threshold secret sharing scheme for distributed RFID environment is proposed.
Because the code division multiple access technology has good confidentiality, anti-interference and multi-access communication capabilities, the literature [13] uses the authentication key and Hash function to design a secure authentication protocol for RFID systems based on code division multiple access technology. Not only can it effectively solve the collision problem of labels, but also resist various attacks including retransmission, tracking, blocking and tampering.
4 Conclusion
Due to the advancement of RFID technology and the rapid decline of cost, RFID systems have been widely used in various fields, but the increasingly prominent security issues of RFID affect the further application of RFID. To this end, this paper analyzes the security problems and solutions of RFID systems. We have reason to believe that RFID security issues can be solved by RFID technology, RFID system design, encryption technology, security awareness, security management and other means. .
APM satisfies High Voltage DC Power Supply application demands, allowing the SP series to cover a voltage range from 0V to 800V. It delivers advanced features. The compact 2U high 19inch wide Adjustable DC Power Supply were designed to meet the needs of both system integrator and bench top users.
Some features of the Switch Mode Power Supply as below:
- Ultrafast respond time and high efficiency
- Accurate voltage and current measurement capability
- Constant Power and wide range of voltage and current output
- Equips with LIST waveform editing function
- Compliant with SCPI communication protocol
- Support RS232/RS485/LAN/USB (standard) ,GPIB (optional)
- Built-in standard automobile electrical testing curves
- Full protection: OVP/OCP/OPP/OTP/SCP
- Voltage drop compensation by remote sense line.
- Have obtained CE,UL,CSA,FCC.ROHS
800V DC Power Supply,Smps Power Supply,Variable Voltage Power Supply,DC Adapter Power Supply
APM Technologies (Dongguan) Co., Ltd , https://www.apmpowersupply.com